
In todays digital age, cyber threats are continually evolving, Endpoint Detection and Response (EDR) has emerged as a cornerstone of cybersecurity strategies. EDR solutions are crucial for monitoring, detecting, and responding to threats on endpoints, offering unparalleled visibility into the security state of each device within an organization. These solutions not only alert security teams to potential threats but also provide detailed insights into threat patterns, helping to bolster defenses against future attacks.
One of the biggest threats to endpoint security is malware, often delivered through malicious files. These files can wreak havoc in a multitude of ways, compromising the integrity of individual endpoints and, potentially, the entire network. Here are several ways malicious files can negatively impact an endpoint or network:
- System Compromise: Malicious files can execute code that compromises the system, allowing attackers to gain unauthorized access. This can lead to further exploitation, such as installing additional malware or stealing sensitive information.
- Data Breach: Once an endpoint is compromised, attackers can exfiltrate sensitive data, leading to significant financial and reputational damage to the organization.
- Ransomware: Malicious files can encrypt files on the endpoint, with attackers demanding a ransom for decryption keys. This not only puts critical data at risk but also leads to operational downtime.
- Botnet Recruitment: Compromised endpoints can be added to a botnet, a network of infected devices used by attackers to launch further attacks, such as DDoS attacks or spam campaigns.
Understanding Wazuh’s File Integrity Monitoring and VirusTotal Integration
File Integrity Monitoring (FIM) is a cornerstone of endpoint security, ensuring that unauthorized modifications to files and directories are detected promptly. Wazuh enhances this capability by providing the option to integrate with VirusTotal, a global threat intelligence platform that utilizes multiple antivirus engines and URL/domain blocklisting services to identify malicious content.
Afterall, if you’re going to have an antivirus, why not have all of them combined into one.
The Operational Flow
- Monitoring and Alerting: Wazuh’s FIM constantly monitors specified directories for any additions, changes, or deletions. Each monitored file’s hash is stored, enabling Wazuh to detect modifications accurately. Upon detecting a change, an alert is generated.
- VirusTotal Integration Activation: When a FIM alert is raised, Wazuh’s integration with VirusTotal is triggered. The file’s hash extracted from the alert is sent to VirusTotal via an HTTP POST request.
- Analysis and Response: VirusTotal compares the submitted hash against its database, returning a JSON response indicating whether the file is recognized as malicious by any of its antivirus engines. Based on this response, Wazuh generates specific alerts ranging from no threat detected to identifying the file as malicious based on the consensus of antivirus engines.
Demonstrating the Power of Integration
Scenario:
A malicious actor has scanned your network and found that you have an exposed port used for remote access:
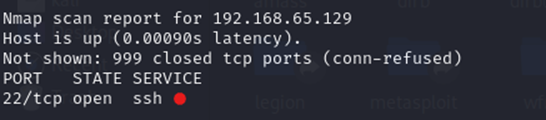
The Hacker opens his favourite Kali Linux tool for breaking into this port (in this case, Metasploit):

As you can see, the configurations here are simple. The attacker configures the MSF script he wants to use, configures the victim IP and chooses his favorite password list:
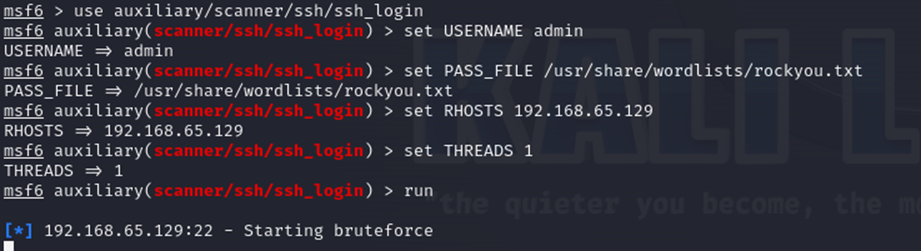
Finally, after the hacking tool establishes a connection, the attacker uses remote access to download a known malicious file to the victim. In this case, for the demonstration, it was the EICAR malware test file used to test malware detection systems.

Here, you see the logs indicating (from bottom to top) the events that occurred in reaction to the malware injection. Here’s what happened:
- There was a file added to the root directory and the FIM spooled up VirusTotal.
- 66 Anti-Virus engines flagged the file as malicious and then the file was deleted.
- Finally, a notification from the endpoint’s agent stating that the “remove-threat.sh” script was activated and removed the threat from the root directory.
The log files will provide a link to the VirusTotal website for you to further inspect the malicious file to gather more intelligence on the intent and purpose of the threat actor.

Tying It All Together: The MITRE ATT&CK Framework
In addition to detecting and responding to threats, Wazuh’s integration with VirusTotal offers insights that can be mapped to the MITRE ATT&CK framework. This framework provides a comprehensive matrix of tactics, techniques, and procedures (TTPs) used by threat actors, enabling security teams to understand and prepare for potential attack vectors.
By analyzing the alerts generated through the VirusTotal integration, security teams can identify the TTPs associated with detected malware, enriching the contextual understanding of threats. This integration not only strengthens the immediate security posture but also contributes to strategic planning and defense optimization.
For example, the MITRE ATT&CK TTP that was correlated with the event in the demonstration was T1203. You can check it out at the following link and see all the many threat actor groups associated with it. It also provides a list of recommended mitigations to prevent the attack in the future.
https://attack.mitre.org/techniques/T1203/
Conclusion
The integration of Wazuh’s File Integrity Monitoring with VirusTotal represents a significant leap forward in endpoint security. This combination offers a proactive, intelligent approach to detecting and responding to threats, underpinned by the global threat intelligence of VirusTotal. By leveraging this integration, organizations can enhance their defense mechanisms, ensuring a robust security posture against an ever-evolving threat landscape.
References:
https://documentation.wazuh.com/current/proof-of-concept-guide/detect-remove-malware-virustotal.html