
Introduction
Cloud hosting has shifted remote management from a luxury to a necessity, given the physical distance from data centers. Traditional remote management tools, such as Remote Desktop (RDP) for Windows users and Secure Shell (SSH) for those on Unix-like systems, along with the strategic use of Bastion hosts for enhanced security, form the backbone of this approach. My entry into the cloud realm was guided by “Network Chuck” on YouTube, who frequently demonstrated the ease of opening SSH port 22 on Linode Cloud instances without accompanying encryption keys. This experience underscored the critical importance of implementing RSA encryption keys for SSH connections, particularly for a port as frequently targeted as port 22.
Handling these keys—ensuring they’re both managed properly and that the port is securely closed after use and equipped with whitelisting—is vital to fend off potential attacks. Attackers, keenly aware of the public IPs used by cloud services, often scan for open ports to exploit through brute force or dictionary attacks. Beyond the mere exposure of these ports, the protocols themselves can present vulnerabilities that attackers might leverage for privilege escalation, lateral movement, data exfiltration, or even deploying ransomware.
SSH/RDP Access
Explanation: Secure Shell (SSH) for Linux/UNIX-based systems and Remote Desktop Protocol (RDP) for Windows-based systems are traditional methods for remote administration. They require opening inbound ports (22 for SSH, 3389 for RDP).
Security Features
- Authentication: SSH offers key-based authentication, a secure alternative to passwords. For RDP, security hinges on strong passwords and multi-factor authentication (MFA).
- Encryption: Both protocols encrypt data in transit, safeguarding against interception and attacks.
Vulnerabilities
- Port Exposure: Open ports, such as SSH (22) and RDP (3389), are beacons for attackers, inviting brute force and network-level attacks.
- Credential Management: The challenge of managing SSH keys and RDP credentials, especially at scale, can lead to increased risks of exposure.
Mitigation Strategies
- Restrict access to SSH/RDP to known IP addresses.
- Implement strong, unique passwords and MFA for RDP.
- Regularly rotate and audit SSH keys.
Bastion Hosts
Explanation: A bastion host is a dedicated instance that acts as a primary access point to other instances in private subnets, reducing the need to expose each instance to the internet.
Security Features
- Centralized Access Point: A single, secured entry point reduces the exposure of instances to the internet.
- Network Segmentation: Acts as a bridge to instances in private subnets, providing a layer of isolation.
Vulnerabilities
- Single Point of Failure: A compromised bastion host can endanger the entire network.
- Management Overhead: Requires continuous management efforts, including securing access and applying updates.
Mitigation Strategies
- Harden the bastion host by minimizing its functionalities.
- Ensure regular updates and patching.
- Employ MFA and SSH key pairs for secure access.
Introducing AWS Systems Manager (SSM) for Secure Remote Management
AWS Systems Manager presents a paradigm shift in how we approach remote management. Its Session Manager service eliminates the need for traditional methods, offering a secure, efficient alternative.
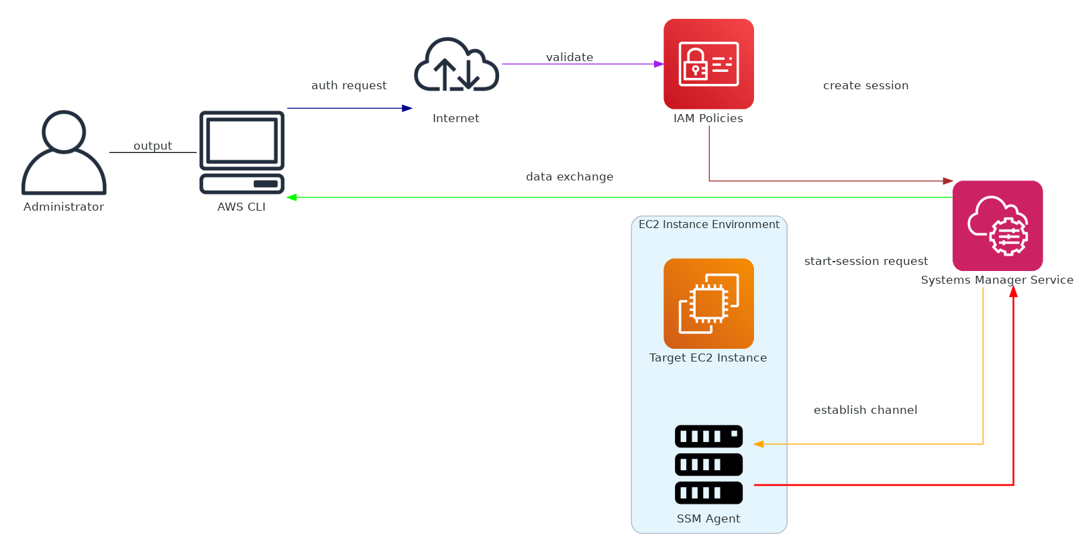
Why AWS Session Manager is a Game-Changer
- Encryption in Transit: All data transmitted between the AWS CLI, Systems Manager service, and the SSM Agent is encrypted in transit over HTTPS using TLS (Transport Layer Security). This ensures that sensitive information remains secure, maintaining confidentiality and integrity during transmission.
- No Open Ports Required: Session Manager operates without requiring any inbound ports to be open on the EC2 instance. This method eliminates the need for traditional SSH or RDP ports to be exposed, significantly reducing the attack surface and enhancing security.
- Logging and Auditing: Integration with AWS CloudTrail and Amazon CloudWatch Logs allows for comprehensive logging and auditing of all Session Manager activity. Every command executed and every interaction is recorded, enabling detailed auditing and compliance tracking.
- IAM-Based Access Controls: Access to instances via Session Manager is meticulously controlled through AWS Identity and Access Management (IAM) policies. This setup allows for fine-grained access control based on the principle of least privilege, ensuring that users and services only have the permissions essential for their roles.
- Centralized Identity Management: By leveraging AWS Single Sign-On (SSO) with Multi-Factor Authentication (MFA), management of access keys is eliminated. This centralized approach simplifies user access management and enhances security by requiring additional authentication factors.
Getting Started with AWS Session Manager
Starting with AWS Session Manager is straightforward, requiring only a few steps to set up secure remote access without the vulnerabilities associated with traditional methods.
You can download my user guide for Assigning IAM Roles to your EC2 Instances for SSM here:
https://jordansuserguidebuck.s3.ca-central-1.amazonaws.com/AssigningIAMRolesForSSM.pdf
You can download my user guide for Setting up AWS CLI using SSO and MFA here:
https://jordansuserguidebuck.s3.ca-central-1.amazonaws.com/SettingUpAWSCLISSO.pdf
For detailed guidance, AWS documentation offers comprehensive resources to help you integrate Session Manager into your AWS environment:
https://docs.aws.amazon.com/systems-manager/latest/userguide/what-is-systems-manager.html
The Takeaway
The landscape of remote management is evolving, with AWS at the forefront of simplifying and securing access to cloud resources. AWS Session Manager stands out as a testament to AWS’s commitment to security, offering an innovative solution that addresses the shortcomings of traditional remote access methods.
Leave a Reply