
Let’s Conduct a Recce
Recce, pronounced like “recky,” is the Canadian Armed Forces’ abbreviation for reconnaissance. It’s a crucial step in battle procedure and it is aimed at gathering intelligence about a specific target. As a former CAF communication specialist, I’ve planned communication requirements for such activities. Understanding the dynamic nature of recce operations is vital for these plans. This concept of reconnaissance also applies in the realm of cybersecurity, particularly for ethical hacking and penetration testing operations.
It’s Not So Different
A key aspect of recce activity is circling the objective to find different angles, identifying points of interest, weapons caches, demographics, patterns of life, and vulnerabilities in defenses. This tactic, known as the clover leaf, involves teams moving towards an objective into an OP (observation post), observing, and then looping around to another OP, sort of resembling the shape of a clover leaf. Avoiding detection during these movements is crucial.
Drawing on this background, I’ve applied similar principles to conduct a thorough reconnaissance of my website, blog.offgridtech.xyz. Instead of physical OPs, I utilized a suite of OSINT tools native to Kali Linux, such as Maltego, whois, whatweb, nmap, sslyze, and chrome dev tools, each offering unique insights into the digital landscape of my web application.
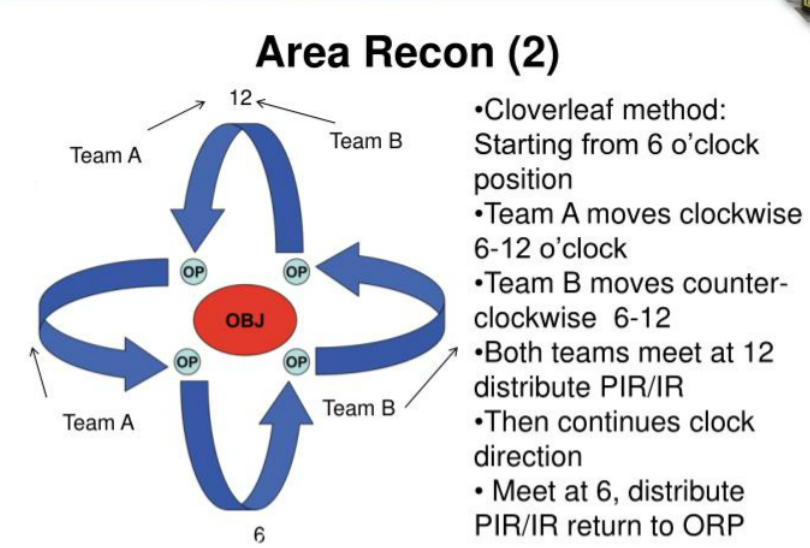
Avoiding Detection = Managing Attribution
In the digital world, every action online leaves a trace, often referred to as a digital signature or “attribute.” Managing attribution is critical, especially for activities where anonymity and discretion are paramount. Techniques for stealth and security in digital reconnaissance include:
- Kasm Workspaces: For secure, isolated digital environments that stream to your web browser.
- Proxies and Proxy Chains: To mask real locations and ensure anonymity.
- TOR Network: Enhancing privacy and making tracing difficult.
- Timing and Pacing: To avoid recognizable patterns in online activities.
- Fake Identities: For preserving operational security during online interactions.
- Use Passive Tools: Tools that only gather information.
The Plan
A plan must be simple, memorable, and easy to follow. I often draw inspiration from a quote I read in a dining facility in Fort Bragg which was inspired by events from WWII:
“After the demise of the best Airborne plan, a most terrifying effect occurs on the battlefield. This effect is known as the Rule of LGOPs. This is, in its purest form, small groups of 19-year-old American Paratroopers. They are well-trained, armed-to-the-teeth, and lack serious adult supervision. They collectively remember the Commander’s intent as ‘March to the sound of the guns and kill anyone who is not dressed like you…’ …or something like that. Happily, they go about the day’s work…”
Little Groups of Paratroopers (LGOP)
This quote highlights the importance of a shared vision, simplicity in understanding, and the initiative to improvise. Plans can fail, but these elements remain crucial. These Paratroopers need to be told what to do; not how to do it.
Phase 1: Preparation and Planning
- Define clear objectives and scope within legal and ethical boundaries and select appropriate OSINT tools and resources.
Phase 2: Data Collection and Analysis
- Collect data using the OSINT tools defined in Phase 1; then analyze this data to map the digital footprint and identify potential vectors for vulnerabilities.
Phase 3: Reporting and Application
- Compile and report findings with actionable recommendations, collaborating with stakeholders to enhance security or strategy.
Recce Report: Leveraging OSINT Tools
You can view my detailed Recce report where I provide a breakdown of the outputs of each tool used and the actionable insights retrieved from the data:
https://jordansuserguidebuck.s3.ca-central-1.amazonaws.com/BlogRecceReport.pdf
WHOIS
- Description: A tool for querying domain registration information.
- Findings: Revealed privacy protection and AWS hosting for blog.offgridtech.xyz, indicating secure and robust domain management.
SSLyze
- Description: Analyzes SSL/TLS configurations of web servers for security vulnerabilities.
- Findings: Identified strong encryption protocols, but the certificate lifespan exceeds recommended best practices.
Nmap
- Description: A network discovery tool used for security auditing and identifying open ports and services.
- Findings: Detected open ports and server specifics, showing the use of AWS Elastic Load Balancer and Apache on Ubuntu.
WhatWeb
- Description: Recognizes web technologies, including content management systems and server software.
- Findings: Found the site running WordPress and other modern technologies, indicating a contemporary and resilient website structure.
Maltego
- Description: An interactive data mining tool that visualizes physical and digital relationships.
- Findings: Provided a comprehensive digital footprint of the blog, showcasing an extensive web infrastructure.
Chrome Developer Tools
- Description: A set of web authoring and debugging tools built into Google Chrome.
- Findings: Revealed server configurations, content type, and response details for the blog, indicating robust performance and standard security practices.
Takeaway
This unique blend of military recce tactics and digital reconnaissance has underscored the importance of adaptability and strategic thinking in cybersecurity. My transition from battlefield operations to web application security showcases a novel approach to understanding and safeguarding digital landscapes. It’s not just about the tools, but how they are wielded with insight and precision.
Leave a Reply