
Launching my blog was a milestone filled with both excitement and a bit of anxiety. So far, nothing has broken down, which is great. But the reality of managing a digital platform hit me – for all I knew, I could be on the verge of a system snap, and I wouldn’t even know until it was too late. That’s where AWS stepped in, like a lighthouse in the murky waters of digital uncertainty. AWS offers built-in monitoring and logging tools that are more than just fancy gadgets; they are essential navigational aids.
The two Logging and Monitoring tools I will speak about in this blog are CloudWatch and CloudTrail. These tools have not only given me visibility into the inner workings of my blog but also the assurance that I can anticipate and prevent potential issues before they escalate.
CloudWatch: The Monitoring Powerhouse
Starting with Basics
When I first explored CloudWatch, I aimed to create a custom dashboard. The AWS guide was my starting point. CloudWatch’s ability to automatically collect metrics like CPU utilization, disk, and network usage was a game changer for me. The granularity of data, available every 5 minutes provided a comprehensive view of my AWS resources. This is mostly a free service but if you wish to monitor assets down to the exact second and create more custom and refined metrics, that’s where the pay-as-you-go system comes in.
Displaying Metrics Effectively
Crafting an effective CloudWatch dashboard was about choosing the right metrics and displaying them in an understandable format. For instance, using line charts for CPU utilization and network in/out made it easy to spot trends and anomalies. The number widget was a quick way to display status checks, immediately showing if there were any issues with my resources.
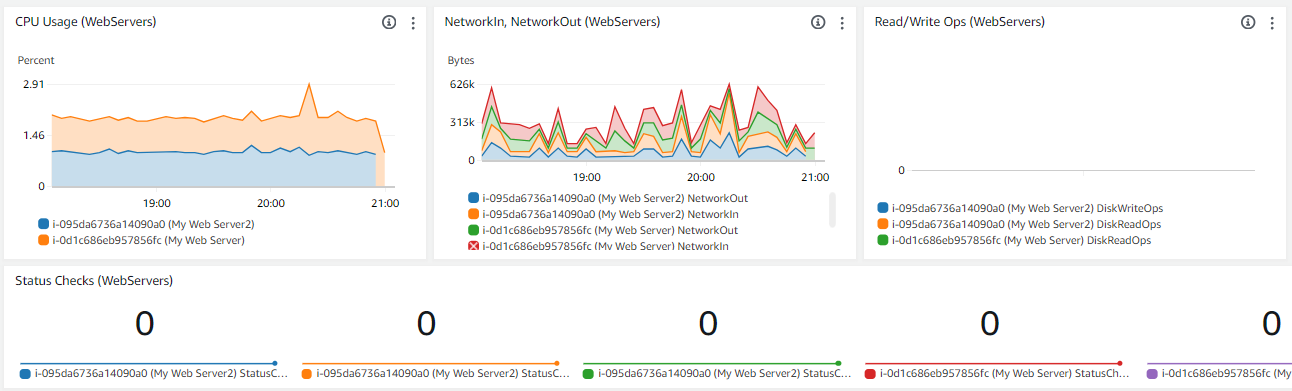
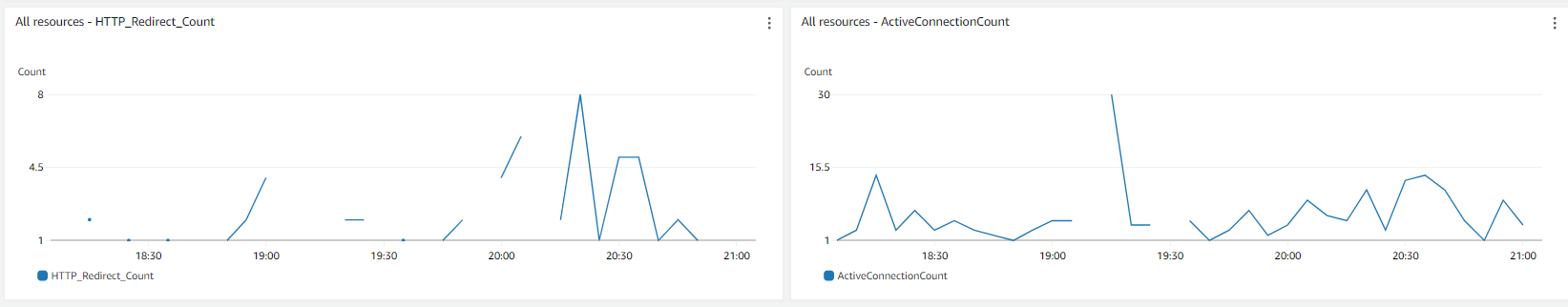
Check out my beginners guide to setting up an effective CloudWatch Dashboard:
CloudTrail: The Compliance and Security Trailblazer
In AWS, it’s crucial to recognize that almost every action taken is, in essence, an API call. This is where AWS CloudTrail plays a pivotal role, diligently monitoring these API calls to provide a comprehensive view of user activities and resource modifications within your AWS environment.
Basic Setup and Security Enhancements
Setting up CloudTrail was straightforward. I enabled the service, created trails, and ensured log file encryption for added security. The process involved selecting an S3 bucket for log storage and integrating CloudTrail with CloudWatch for real-time monitoring.
Log File Analysis
Regularly reviewing CloudTrail logs is a good idea for catching anomalous behavior before it becomes a trend. Of course, manually doing this will become laborious and ineffective. Trust me, as a former CAF Cryptographic Custodian, I have done my far share of manual log inspection. That’s why building specific metrics and triggering alarms can help you track the events that matter to you. For example, alarms for multiple failed login attempts helped me stay on top of potential security threats.
Here is my beginners guide to your introduction of CloudTrail:
https://jordansuserguidebuck.s3.ca-central-1.amazonaws.com/BasicCloudTrailGuide.pdf
Integrating CloudWatch and CloudTrail
Accessing Logs and Creating Metrics
One of my key achievements was integrating CloudTrail logs into CloudWatch. I accessed the CloudTrail log group in the CloudWatch console and used a filter pattern to monitor root user logins. This integration allowed me to create a metric filter and set an alarm for these specific events.
Configuring Alarms
Setting up an alarm based on the root user login events was a critical security measure. I configured the alarm to trigger whenever there was a root user login, indicating a high-level administrative activity. This setup not only enhanced security but also contributed to operational efficiency. Other Alarms I configured were for things like CPU over utilization. I set the threshold to 80% so I can be notified of a potential DDoS or a failure due to misconfiguration of my ELB.
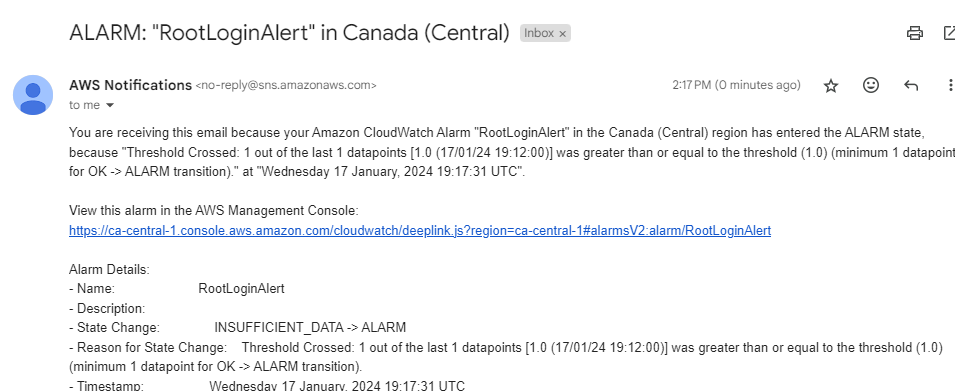
Check out Guide for creating custom metrics with CloudTrail logs and configuring alarms:
https://jordansuserguidebuck.s3.ca-central-1.amazonaws.com/RootUserLoginAlarmGuide.pdf
Takeaway: A Robust Monitoring Framework
My journey with CloudWatch and CloudTrail has taught me the importance of proactive monitoring and security insights. By integrating these two powerful AWS services, I established a robust monitoring framework. This setup has not only enhanced my ability to maintain the security and continuity of my AWS resources but also provided valuable insights for compliance and auditing.
This journey has been about more than just technical setup; it’s been a learning curve in understanding and effectively utilizing AWS’s powerful monitoring and logging capabilities. Whether you’re managing a large-scale enterprise infrastructure or a smaller project, these tools are invaluable in maintaining the health and security of your AWS environment.
Leave a Reply